F3EAD - Acting faster than the enemy can react: QMN035
Martial Mental Models: The Quartermaster, Wednesday, 12 June
(Today’s report is a 5 minute read)
BLUF: F3EAD is probably the most effective operating model to come out of the wars in Afghanistan and Iraq - and stands for Find, Fix, Finish, Exploit, Analyze, and Disseminate. It's a version of previous targeting methodologies that integrates operations and intelligence cycles first to guide activity on the ground with relevant, timely information, and then ensure that intelligence gained by those ground troops goes immediately back into the intelligence process with deliberate exploitation, analysis and sharing of gained information.
Brady here. In 2007 the US military faced a daunting task. Fighting a war in two austere desert environments against a rapidly evolving adversary who changed tactics on a weekly basis, American forces and their allies faced a simmering civil war in Iraq and a series of seasonal offensives in Afghanistan. Technological advantages only took US troops so far - drones, precision guided bombs and night vision provided more than enough capability for victory in individual firefights, but troops struggled to make headway over time because Al Qaeda changed and reoriented too quickly. US Special Operations Forces (SOF) had to find a way to move faster and compound their successes - and thereby cut enough heads off the hydra to render it ineffective at disrupting elections and nation-building efforts in both Iraq and Afghanistan. How does a massive, bureaucratic and hidebound western Army not only counter a decentralized, innovative and highly motivated transnational terrorist organization, but defeat it on its own territory? SOF leaders perfected a methodology called F3EAD - also known as the SOF targeting process - which did just that.
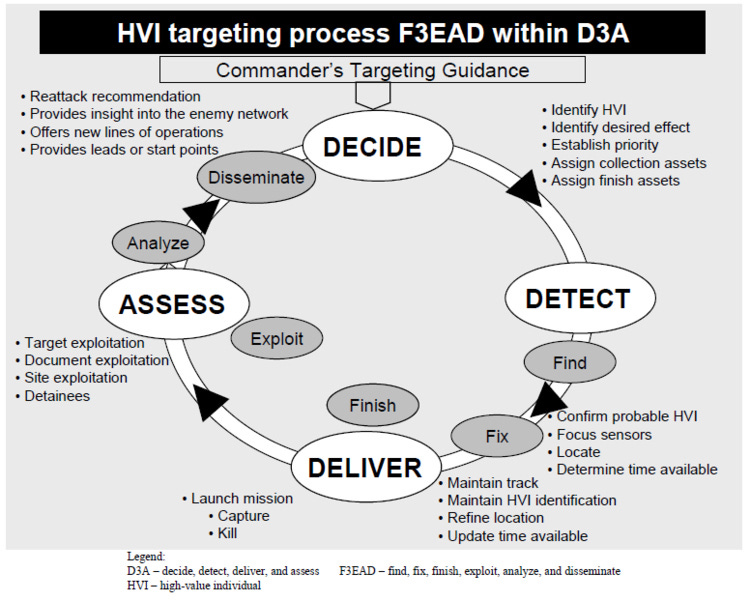
Image Source: RealClearDefense
F3EAD stands for Find, Fix, Finish, Exploit, Analyze, and Disseminate. It's a version of previous targeting methodologies that integrates operations and intelligence cycles first to guide activity on the ground with relevant, timely information, and then ensure that intelligence gained by those ground troops goes immediately back into the intelligence process with deliberate exploitation and analysis of gained information. Analysis and guidance for follow-on operations is then built into the next day’s orders. I'll explain each step here.
Find: Leaders and their intelligence professionals nominate targets for further intelligence gathering. These targets can be individuals, organizations or locations and can be deliberate or targets of opportunity.
Fix: This is the form of the verb meaning “to make firm, stable, or stationary.” Leaders use surveillance and reconnaissance assets to locate and hold the target in time and space while friendly forces can be massed to attack.
Finish: In many cases, forces now close with and destroy or seize the target. But these types of “kinetic” effects aren't always necessary:
“...the finish phase can just as easily be non-kinetic in nature. Neutralization of an enemy communications node, disrupting a courier network, legal prosecution of key terrorist personalities, or achieving a desired psychological, political, or social effect are just as much a part of “finish” as missile strikes or combat assaults.”
In past targeting methodologies the Finish phase was considered the “main effort” - the actions that achieved the intent of the operation. This is where F3EAD is different- for many of the warfighters in the process, the Finish phase was only the beginning of their work.
Exploit: At this point, US forces capture, examine, and analyze enemy information and materiel found at the target’s location (looking a lot like crime scene investigation) and then interrogate and process captured enemy personnel for to gain more timely intelligence. These processes also include using gained evidence for legally prosecuting captured terrorist leaders after the engagement. This phase is often referred to as the real “main effort” of F3EAD.
Analyze: Analysis makes sense of all the information gained in the Exploit phase - filling in as many of the gaps in information as possible and presenting a more complete picture of the larger enemy situation to allow for more effective operations as soon as the next day. Some information can be analyzed locally and some must be sent home for more detailed examination.
Disseminate: Broad information sharing across organizational boundaries inherent in western militaries is key to quickly making the most of all previous efforts by getting ahead of an elusive and distributed enemy. Troops on the ground need to get every piece of valuable intelligence in order to make their next actions effective. Establishment of this policy required a deliberate and considered effort to overcome bureaucratic obstacles to make sure everyone got the information they needed on time.
By developing and applying this methodology for fusing intelligence and operations, US forces were able to systematically dismantle Al Qaeda in Iraq over a few years by focusing efforts on regional leaders that due to their covert and highly mobile strategy had eluded American and allied forces in previous years (Note: though powerful when applied with consistency, F3EAD’s earlier success wouldn’t prevent ISIS from filling the void after Iraq was abandoned). When properly executed, F3EAD enabled commanders at every level to plan and execute operations against the enemy faster than the enemy could react. (BJM)
The best summary of F3EAD can be found at Small Wars Journal by Majors Michael Harris and Charles Faint. (BJM)
IF-THEN REASONING: Amazon launches Personalize, a fully managed AI-powered recommendation service “Customers provide an activity stream from their apps and websites — e.g., clicks, page views, signups, and purchases — in addition to an inventory of the items they want to recommend (such as articles, products, videos, or music) and optional demographic information (like age or geographic location). They receive results via an API and only pay for what they use.” How about Amazon pay customers to provide all that data instead? (KSA)
LIFE CHANGER: David Bellavia prepares for a life changed forever by Medal of Honor (3 min) “That night, Staff Sgt. Bellavia single-handedly saved an entire squad, risking his own life to allow his fellow soldiers to break contact and reorganize when trapped by overwhelming insurgent fire,” the Army’s official narrative states. “He then voluntarily entered and cleared an insurgent strong point, killing four and seriously wounding another.” (BJM)
DANGERS OF A DEFENSE BEHEMOTH: 4 Questions Hovering Over the Raytheon-United Technologies Deal to Create a Defense Giant (3 min) Innovation, competition and price. “The government’s foremost concern is that there is sufficient innovation in the defense sector to design and produce new weapons systems, said William Kovacic, a professor at George Washington University Law School and a former chairman of the Federal Trade Commission. “Any shrinking in the number of these enterprises ought to be a matter of concern for the defense agencies and for government antitrust agencies,” he said.” (BJM)
Remarks Complete. Nothing Follows.
KS Anthony (KSA) & Brady Moore (BJM)


